Managing Personal Data in Emergency Calls
In the DECTS project – funded by NGI TRUST Grant Agreement No. 825618 – OwnYourData and DEC112 implemented a Proof-of-Concept to demonstrate sharing personal data between an emergency caller and a control room.
Problem Description
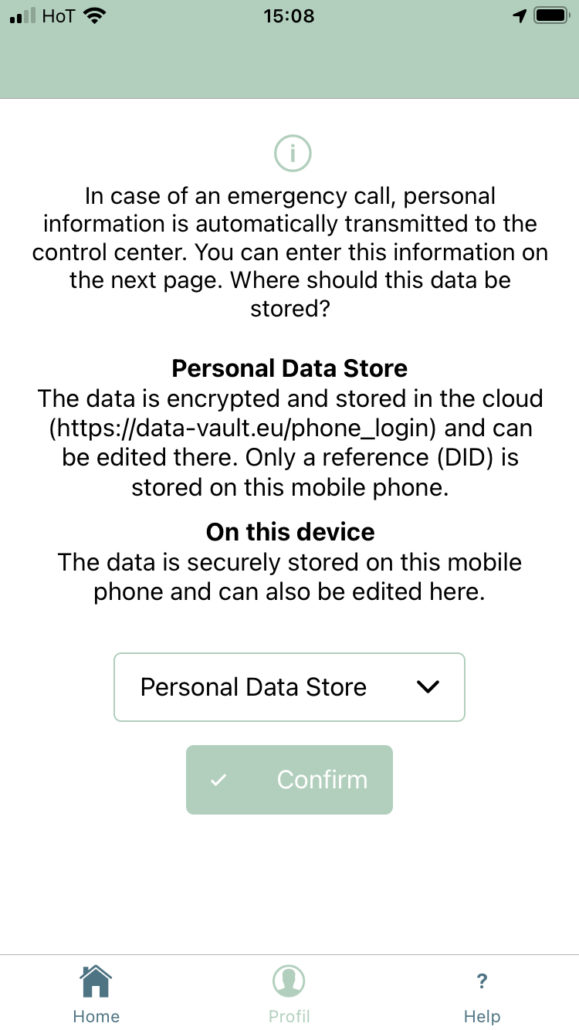
The DEC112 App for deaf emergency chats allows users to store personal information (profile data) at the phone to be automatically shared with an operator in a control room when an emergency chat is initiated. But storing this profile data has a few disadvantages like inability to migrate this data when switching phones and also security concerns (anyone gaining access to this phone can read and edit the data). It therefore makes sense to also provide an option to store this emergency information securely in the cloud which in turn generates several challenges:
- referencing and accessing emergency information in the cloud
- migrating between cloud storage providers (GDPR Article 20 – Right to Data Portability)
- guaranteeing secure storage of profile data
This blog posts describes the implementation of managing profile data in a Personal Data Store addressing the above-mentioned challenges.
Self Sovereign Identity
Decentralized Identifiers (DID) provide an elegant and self-determined way of managing access to personal data. Using cryptographic methods and blockchain technology a user can generate a DID (i.e., a unique token) that references a DID Document. In this document a service endpoint can be specified that provides a certain type of service. Since only the user is in possession of the cryptographic key to manage the DID Document it can be edited only by this user.
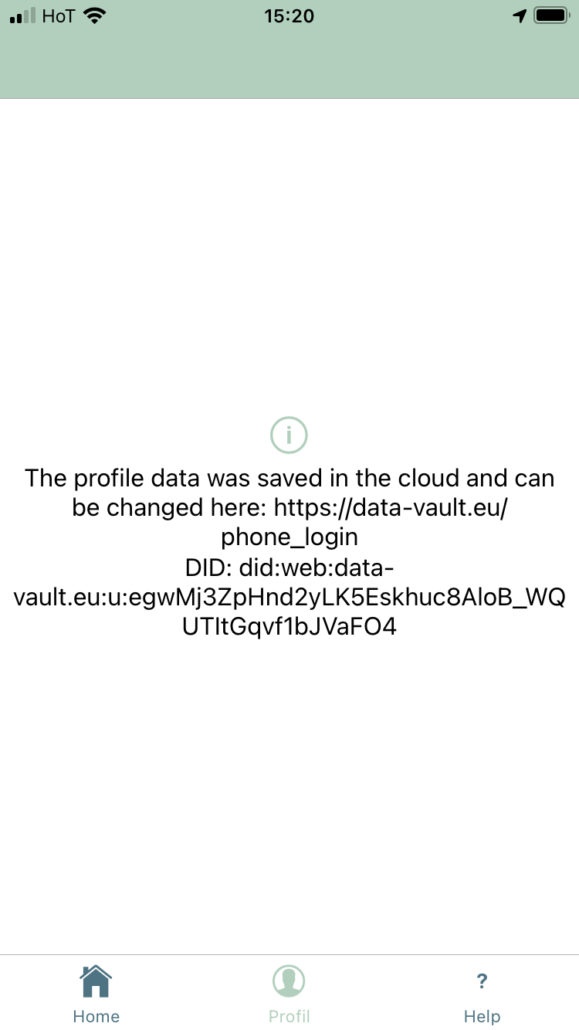
For the given use case of deaf emergency chats the DEC112 app automatically generates a DID at user registration and to reference an account in the OwnYourData Data Vault (source available here: https://github.com/OwnYourData/oyd-pia2). The user has the option to choose between storing the data on the phone or in a Personal Data Store and when choosing Personal Data Store the respective DID is shown on the Profile page.
Shamir’s Secret Sharing
The OwnYourData Data Vault is a Personal Data Store that recently received the MyData Operator Status and is used as the default cloud storage for personal information associated with an DEC112 user account. Since it stores personal data End-to-End encrypted it was necessary to develop a solution to exchange this encrypted data with a control room. The component that manages data provisioning in case of an emergency chat is called PI2 (Personal Identifiable Information) – source code available here: https://github.com/OwnYourData/service-pi2.
Upon creating an account in the OwnYourData Data Vault two key parts a created using the Shamir Secret Sharing scheme. One key part remains in the Data Vault while the other key part is sent to all participating PI2 services located in the respective control rooms. The profile data can only be decrypted when both key parts come together. Additionally, the Personal Data Stores logs any access to the encrypted profile data to guarantee complete documentation.
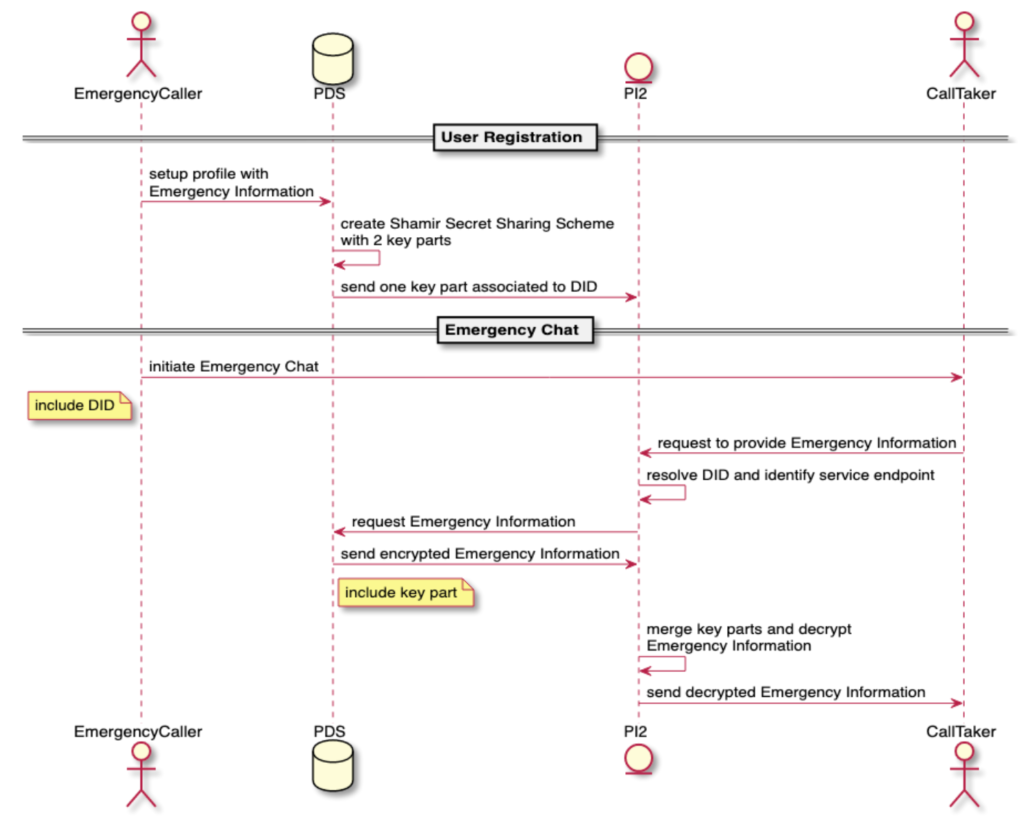
The data flow for accessing profile data during an emergency chat is displayed in the following sequence diagram.
The basic steps in providing personal information upon initiating an emergency chat include:
- The Viewer (client-side application used by the Call Taker) requests from PI2 additional information about the Emergency Call based on the DID delivered along the emergency chat.
- PI2 resolves the DID (i.e., retrieves the DID document) and gets the service endpoint of the PDS holding emergency information
- PDS sends encrypted emergency information together with one key part for decryption
- PI2 combines stored and provided key parts to decrypt emergency information and responds to Call Taker
Conclusions
This blog post described the infrastructure to share data in a secure and self-determined way. Users leverage capabilities of DIDs to manage a trusted service endpoint and use Shamir’s Secret Sharing scheme for a purpose-based data provisioning. A working prototype was implemented for the DEC112 project in Austria.